
i cant keep up with all these cisco security advisories do






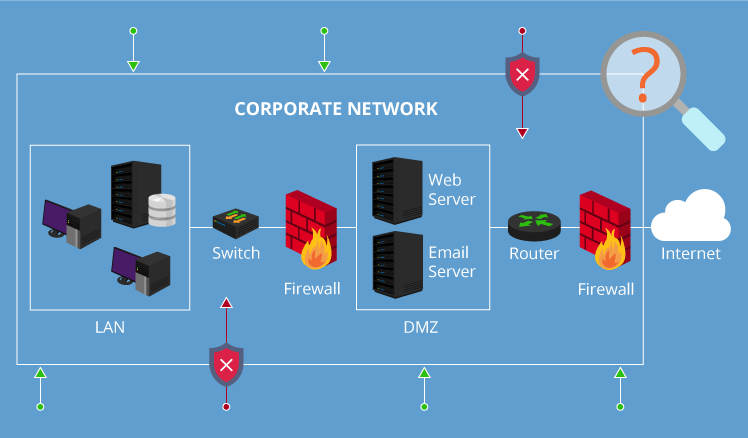


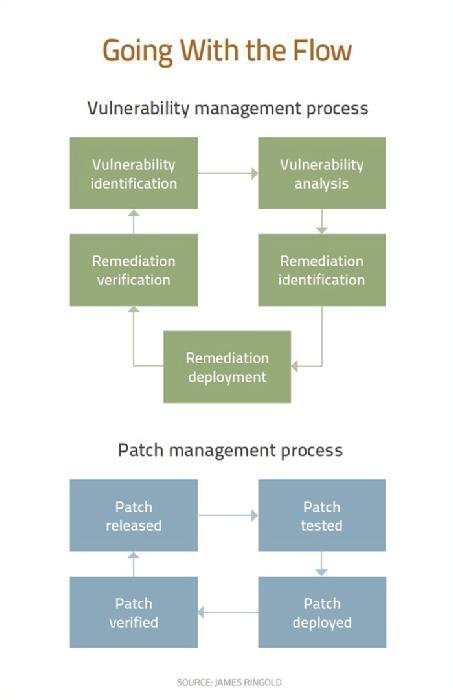


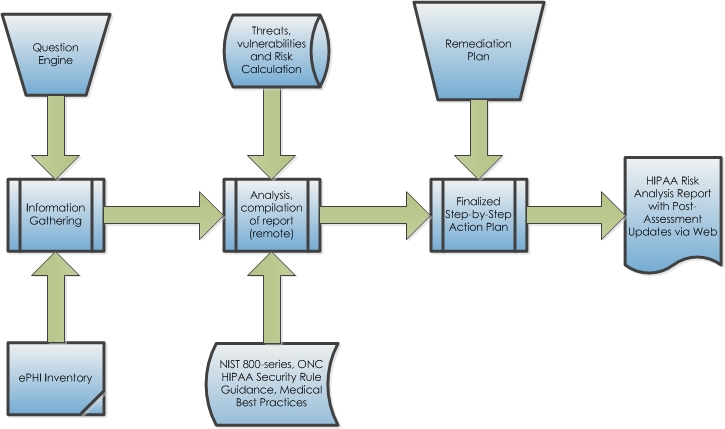

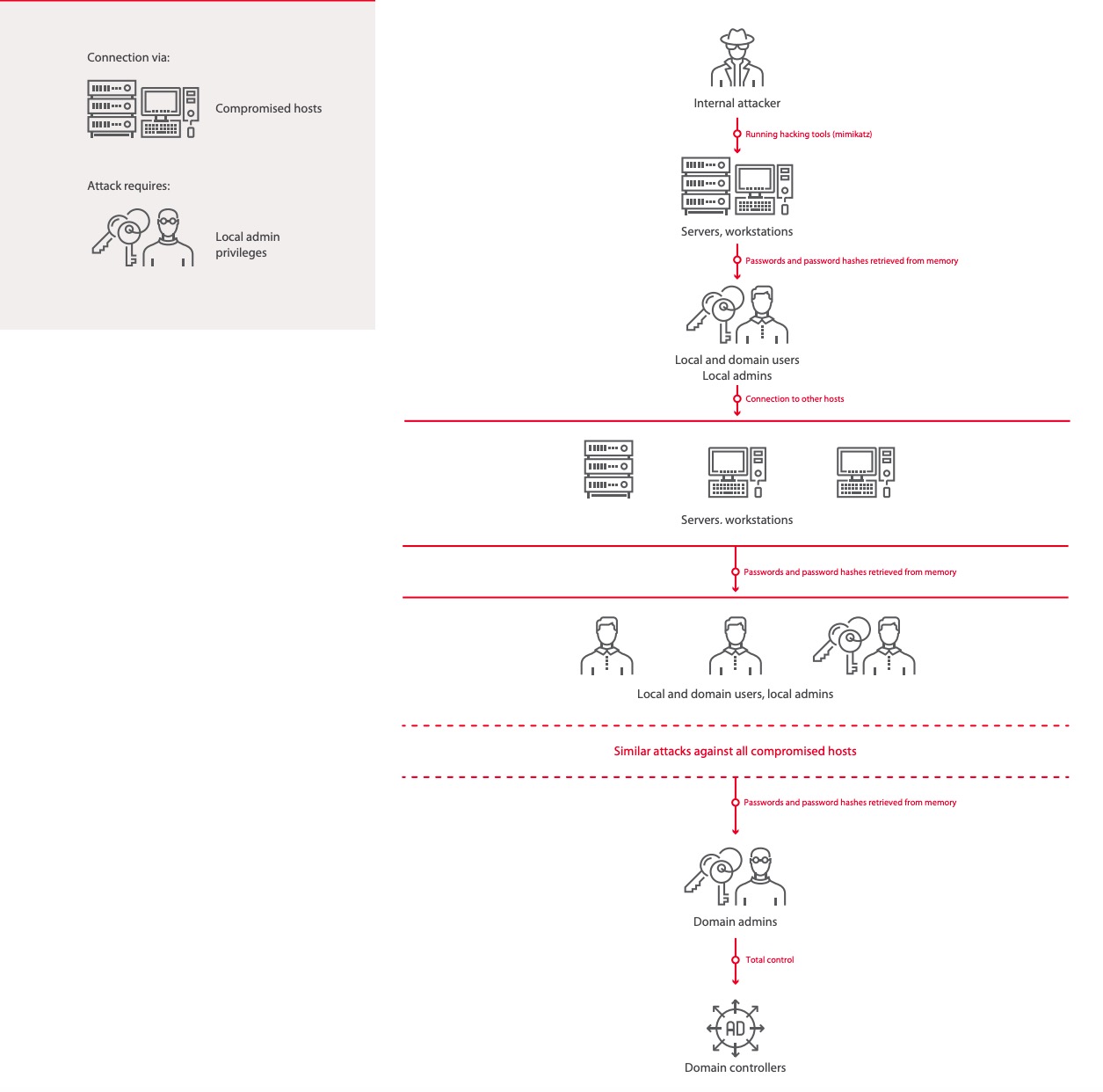

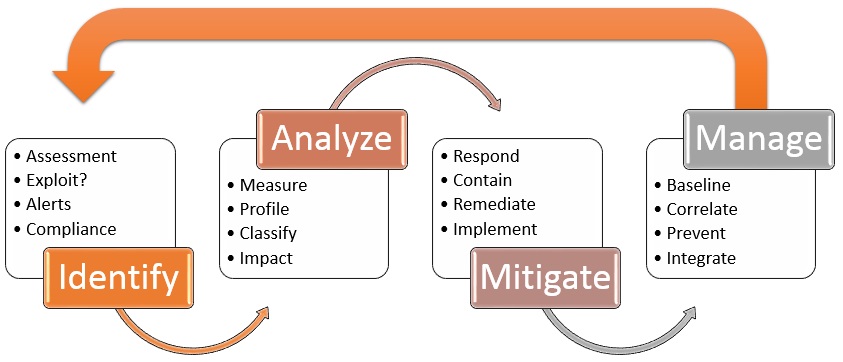








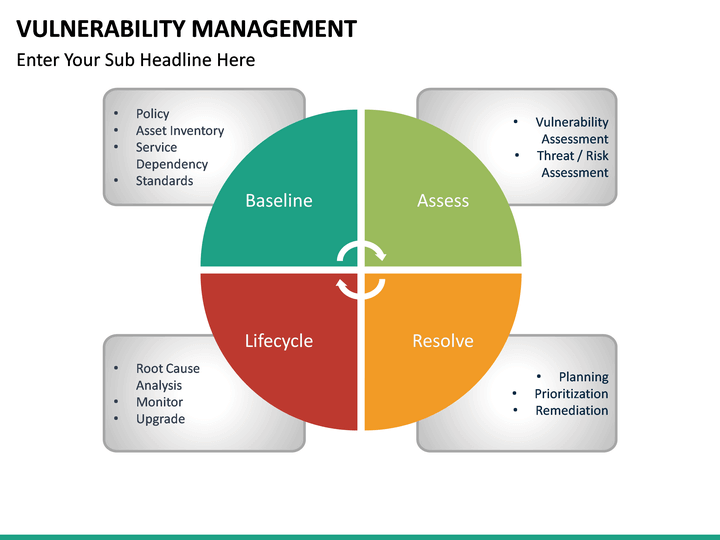



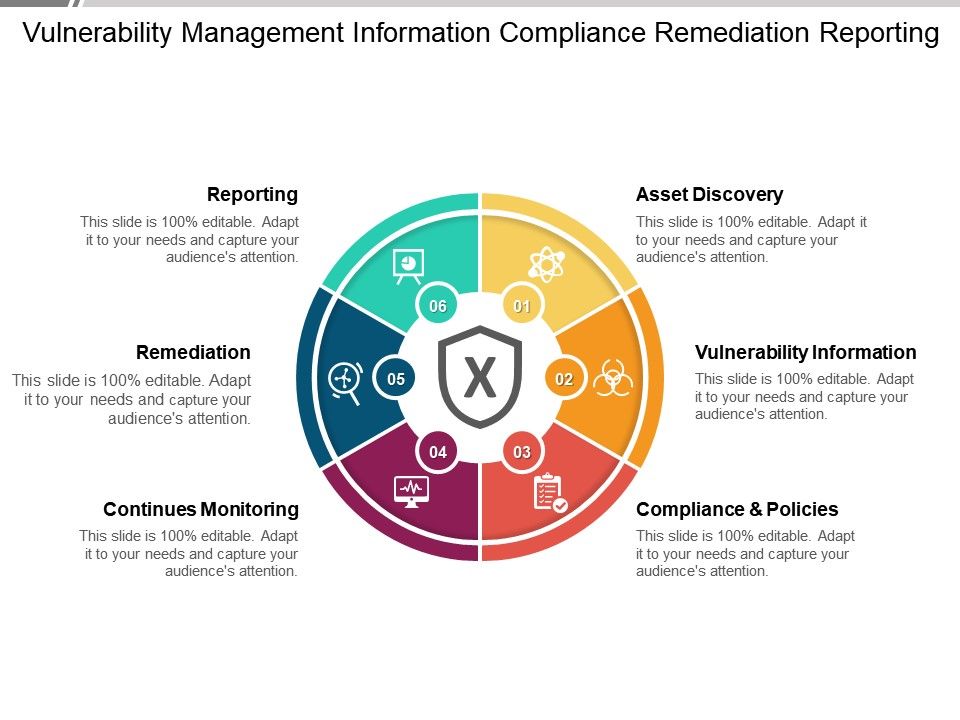

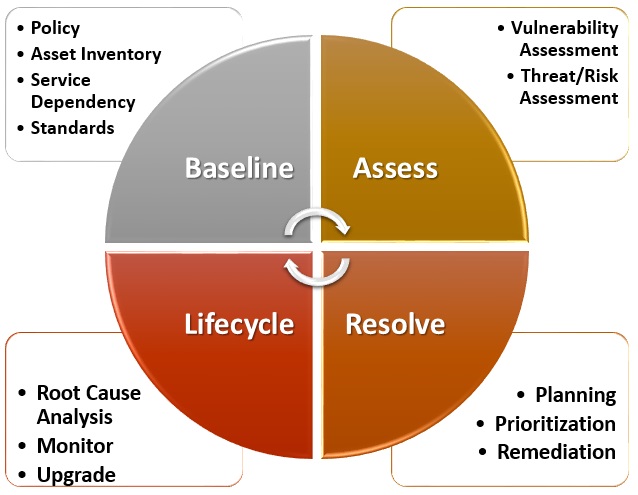

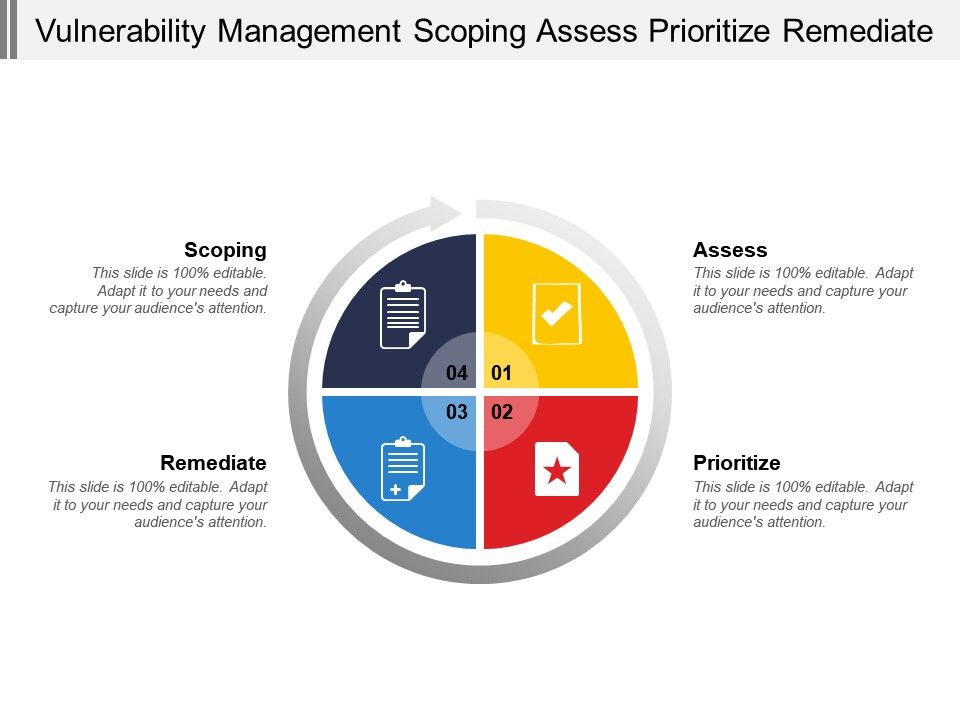





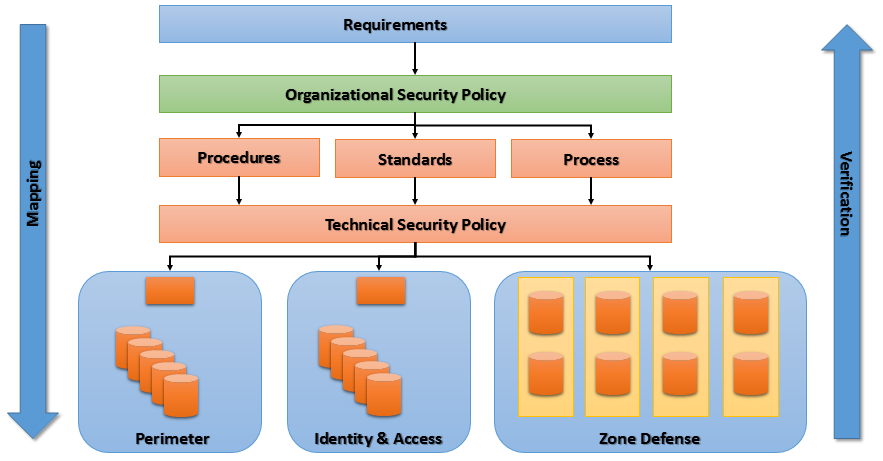
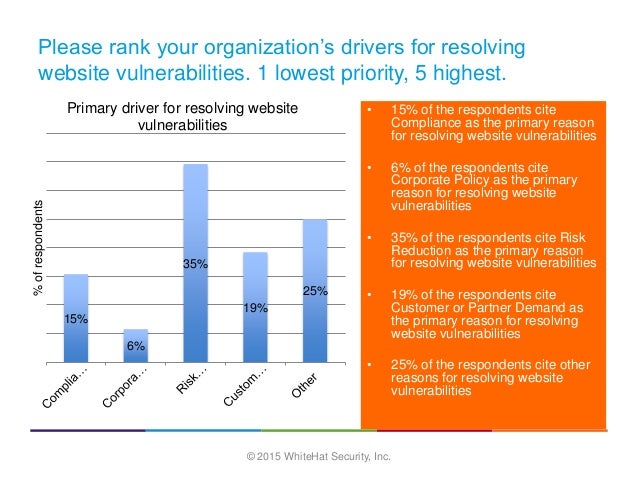

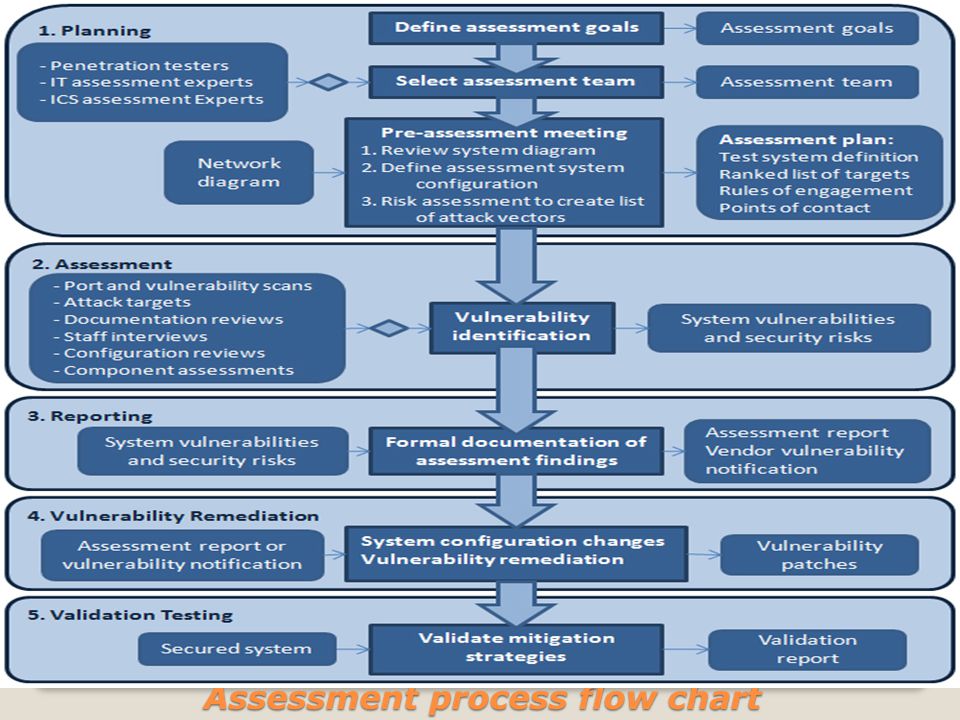 Understanding The Vulnerability Response Application
Understanding The Vulnerability Response Application An Overview Of Vulnerability Assessment And Penetration.
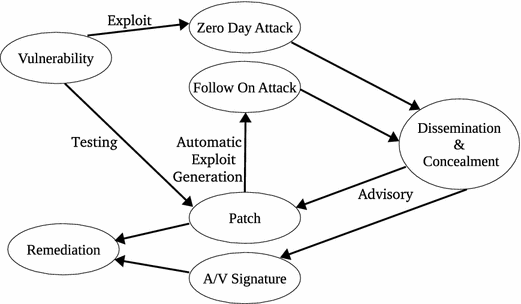
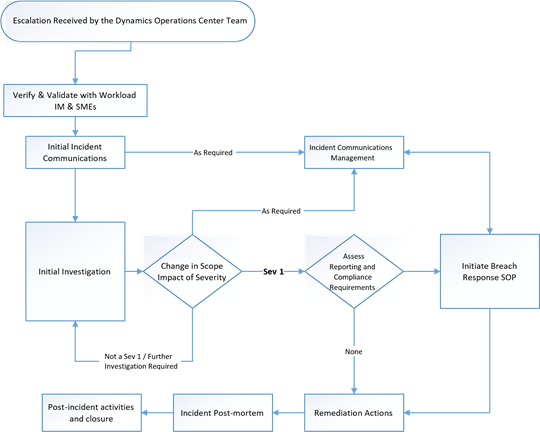
Vulnerability Remediation Process Flow Chart Remediation Workflows.
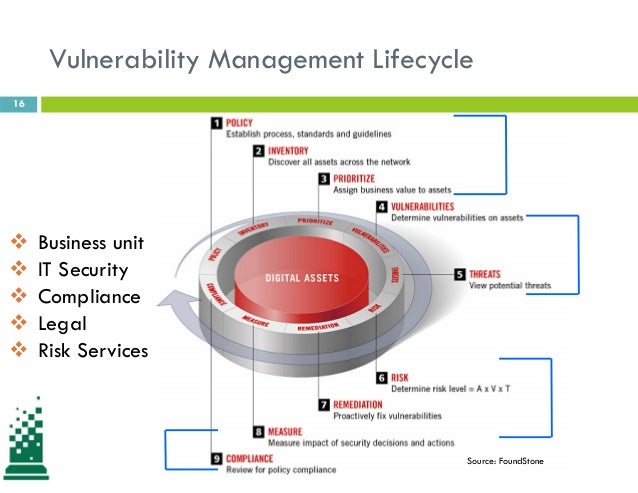
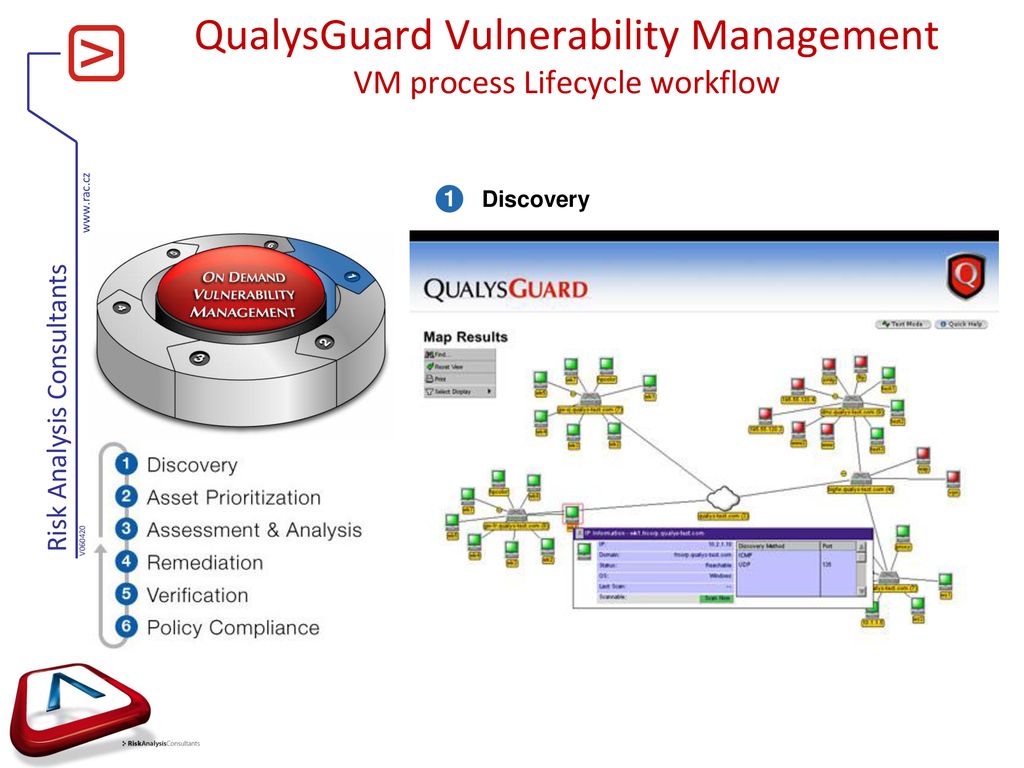
Vulnerability Remediation Process Flow Chart Monitoring Threats For Pci Compliance.
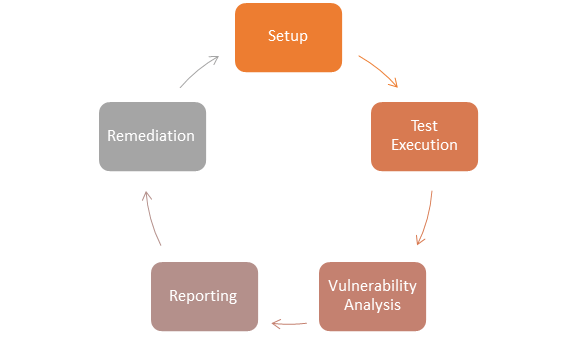
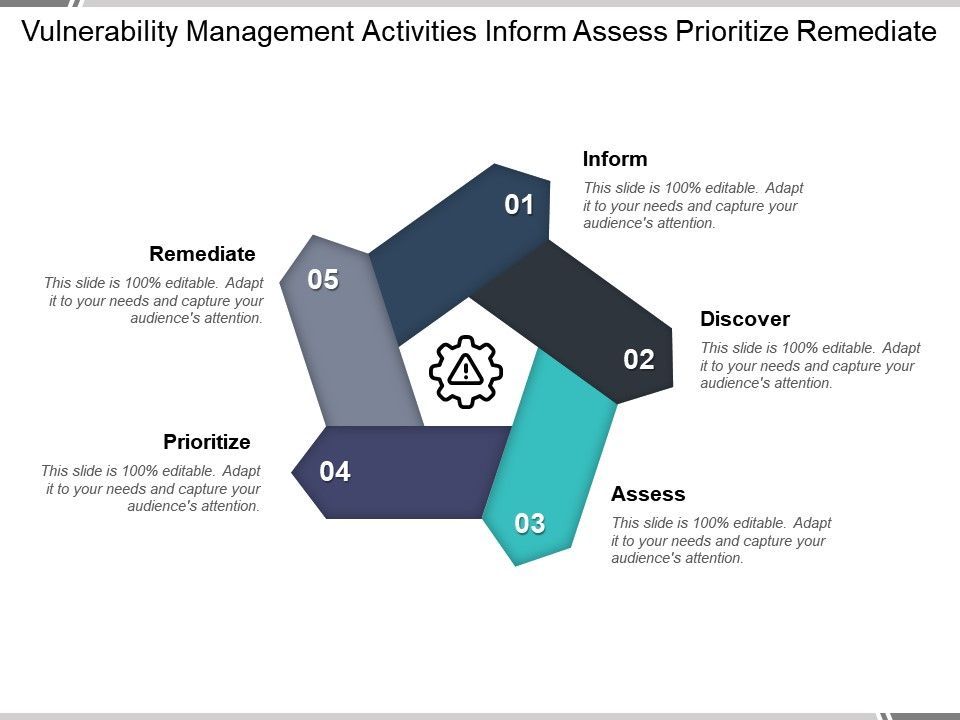
Vulnerability Remediation Process Flow Chart What Is Vulnerability Assessment Testing Process Vapt Scan.
Vulnerability Remediation Process Flow ChartVulnerability Remediation Process Flow Chart Gold, White, Black, Red, Blue, Beige, Grey, Price, Rose, Orange, Purple, Green, Yellow, Cyan, Bordeaux, pink, Indigo, Brown, Silver,Electronics, Video Games, Computers, Cell Phones, Toys, Games, Apparel, Accessories, Shoes, Jewelry, Watches, Office Products, Sports & Outdoors, Sporting Goods, Baby Products, Health, Personal Care, Beauty, Home, Garden, Bed & Bath, Furniture, Tools, Hardware, Vacuums, Outdoor Living, Automotive Parts, Pet Supplies, Broadband, DSL, Books, Book Store, Magazine, Subscription, Music, CDs, DVDs, Videos,Online Shopping