
vdoe leadership organization


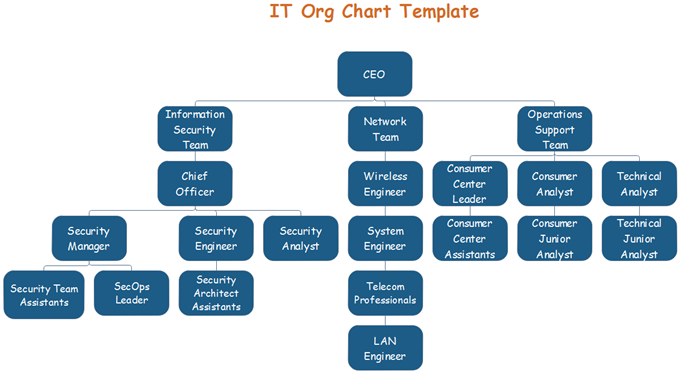
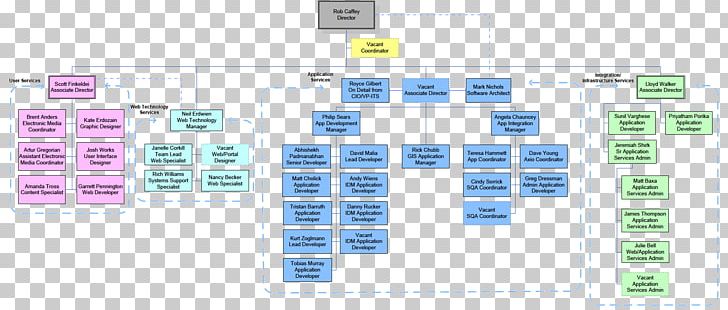

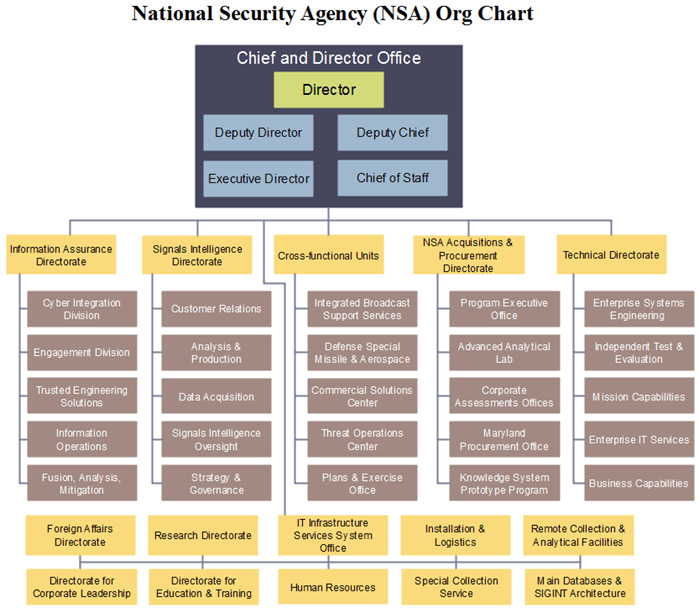



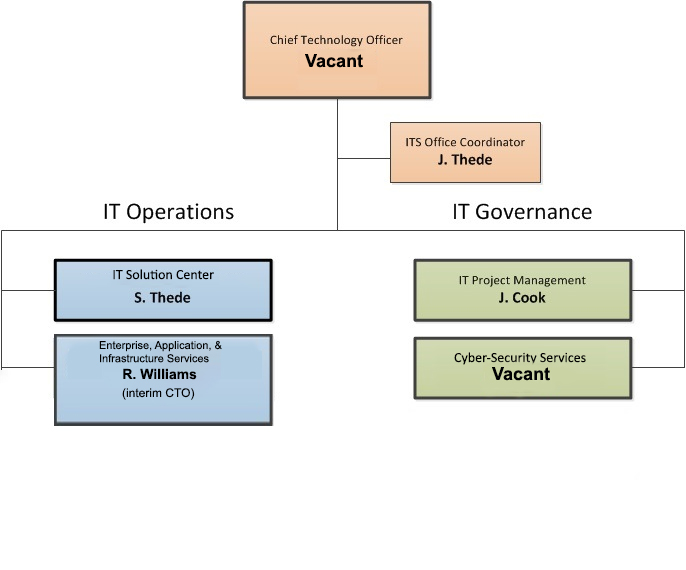
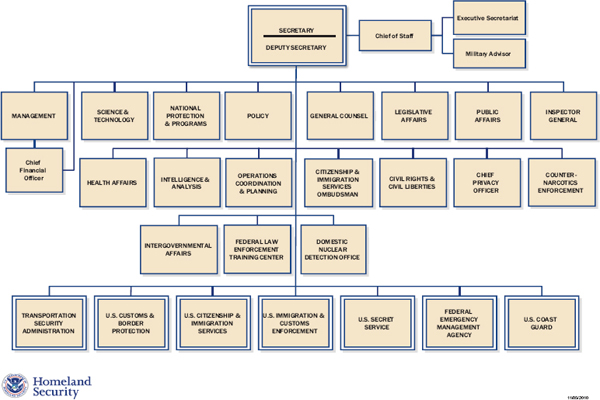



























 Vdoe Leadership Organization
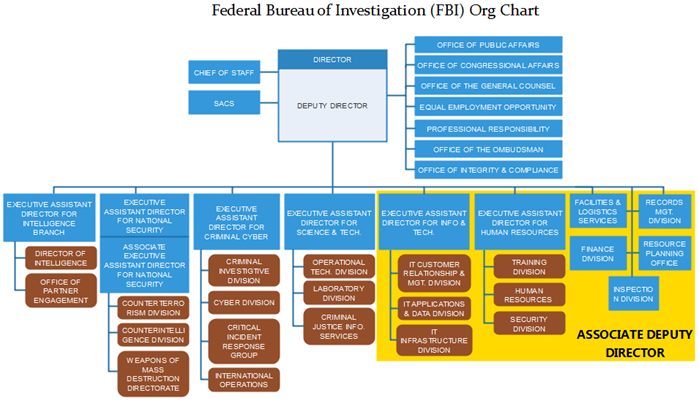
Vdoe Leadership Organization Rex Tillerson Proposes New Cyber Bureau At The State.
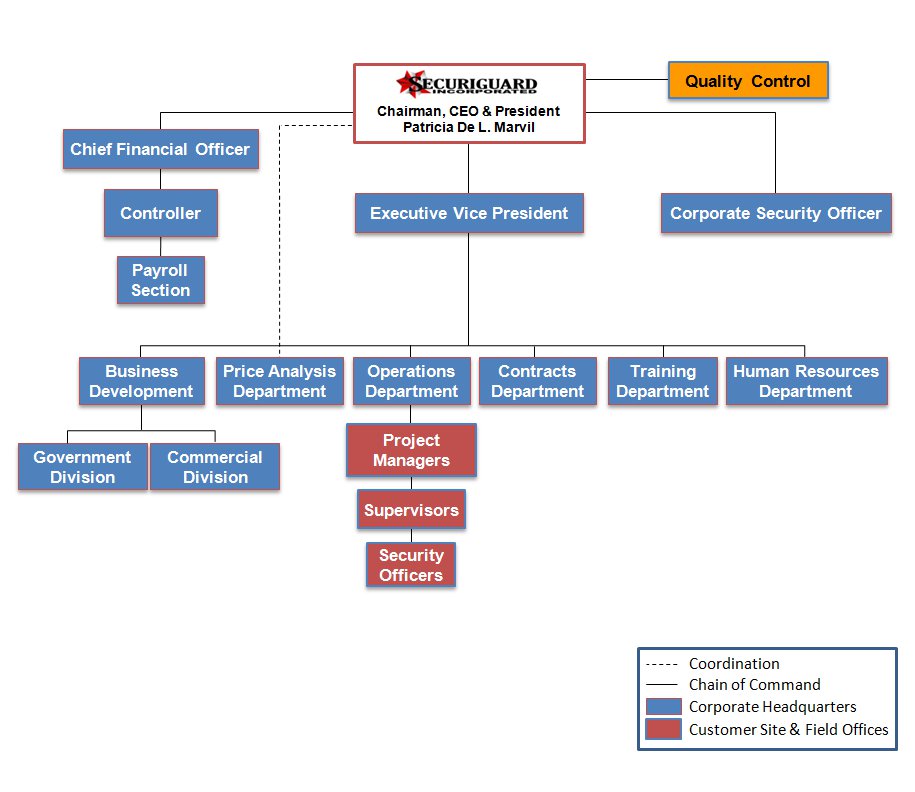
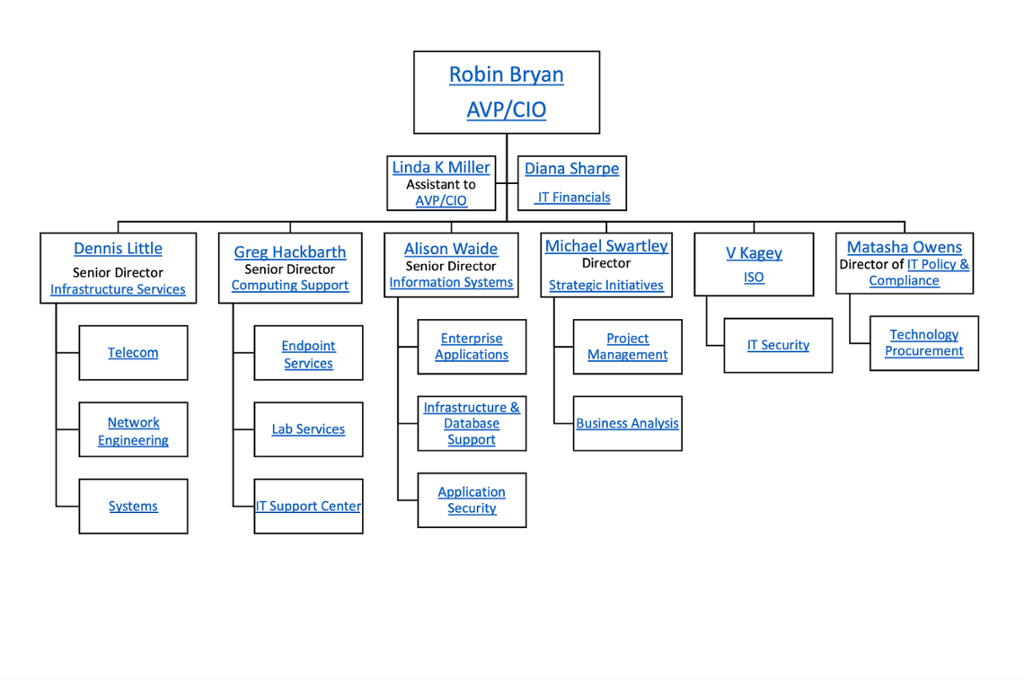
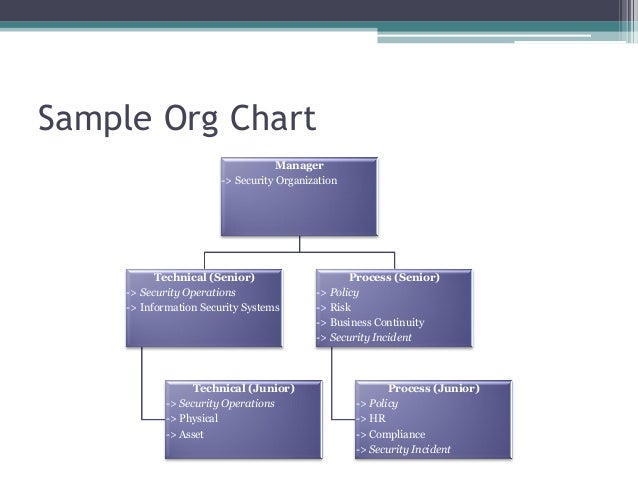
Information Security Organizational Chart University Of Delaware Udit Organization.
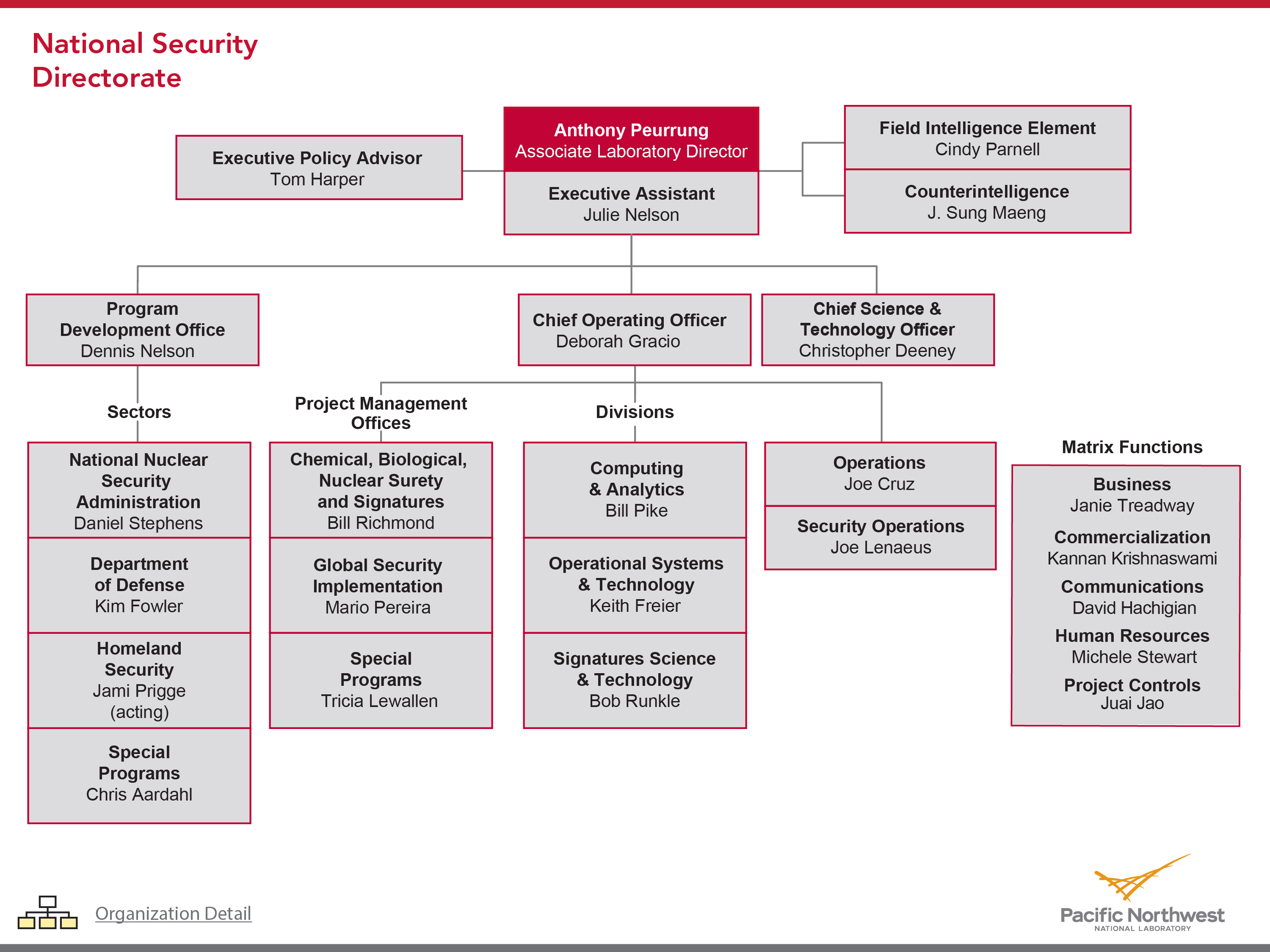
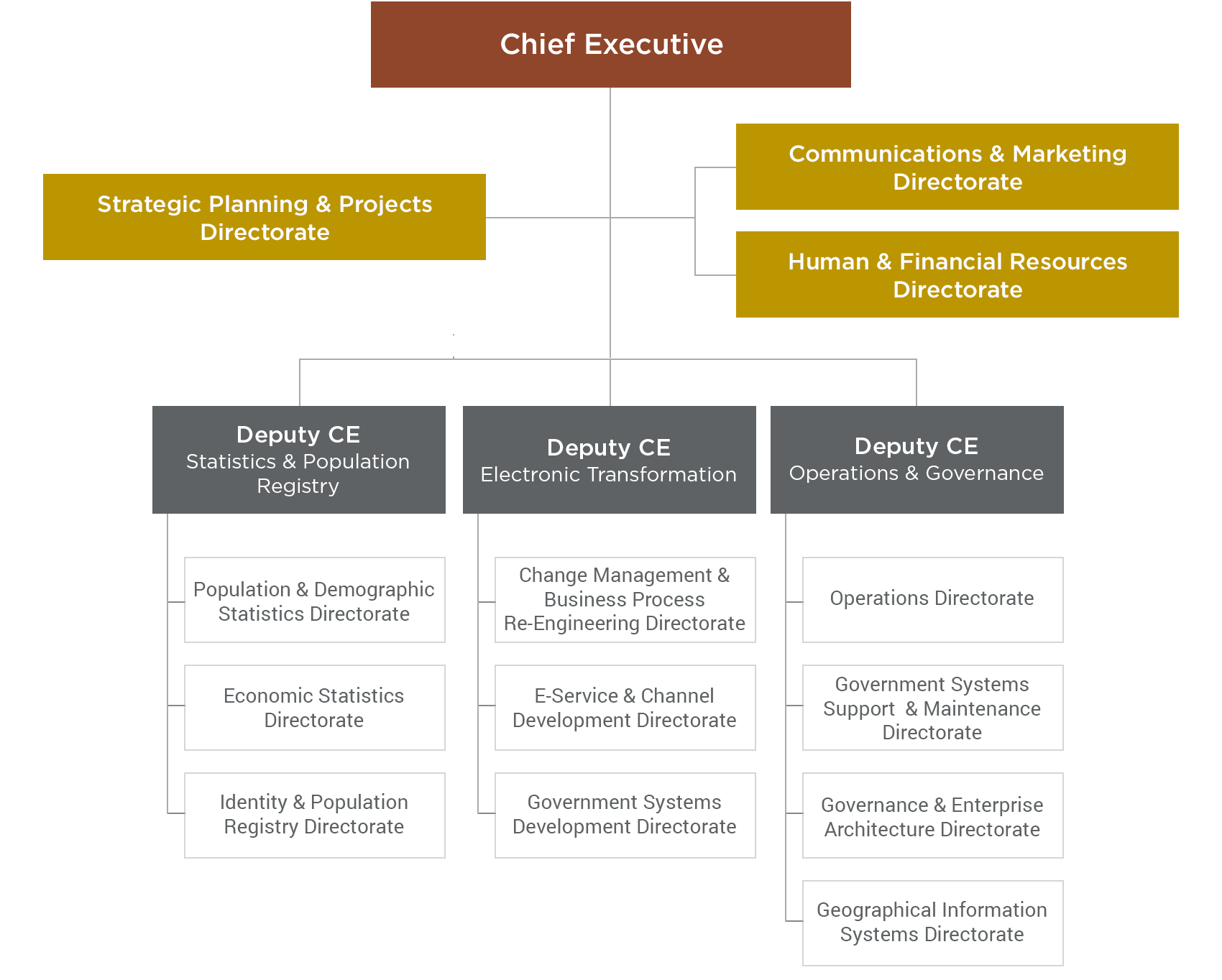
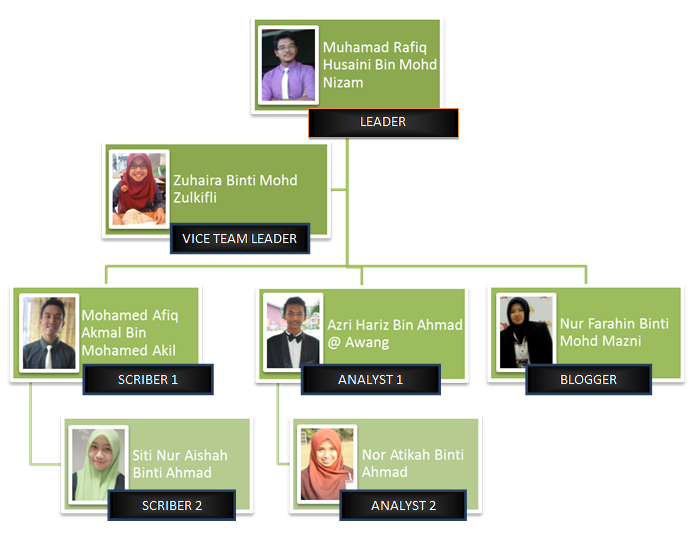
Information Security Organizational Chart Natural Security For A Variable And Risk Filled World.
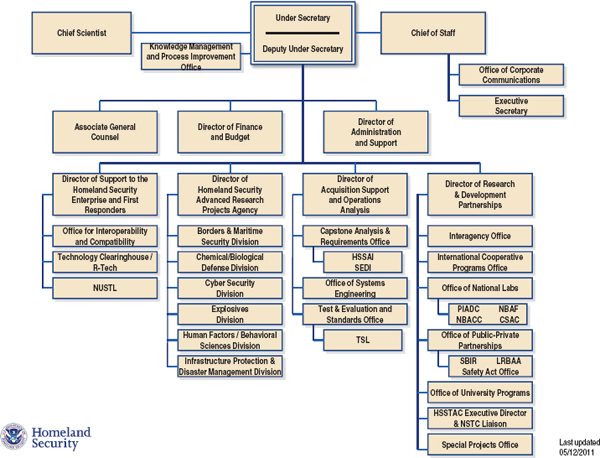
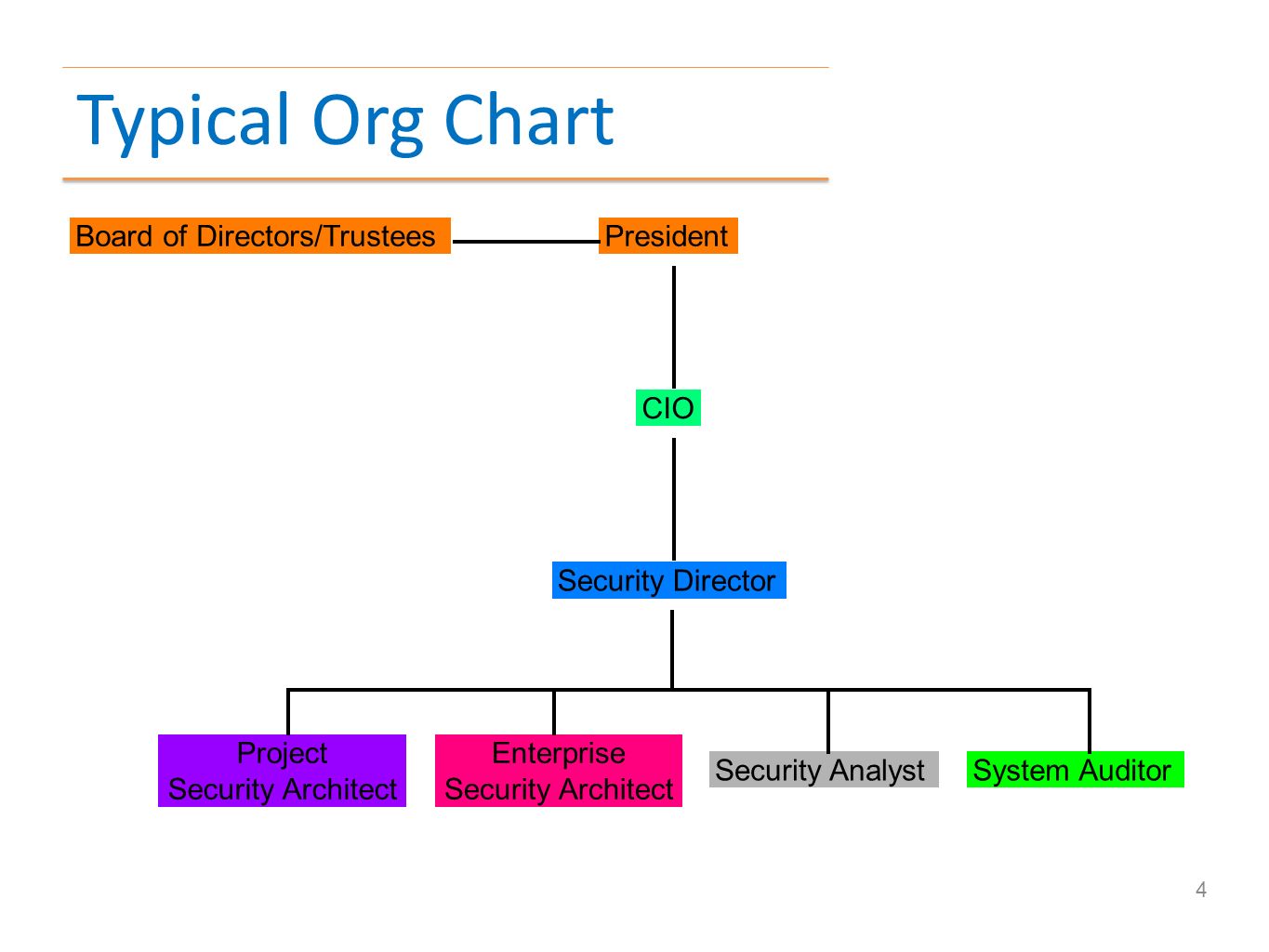
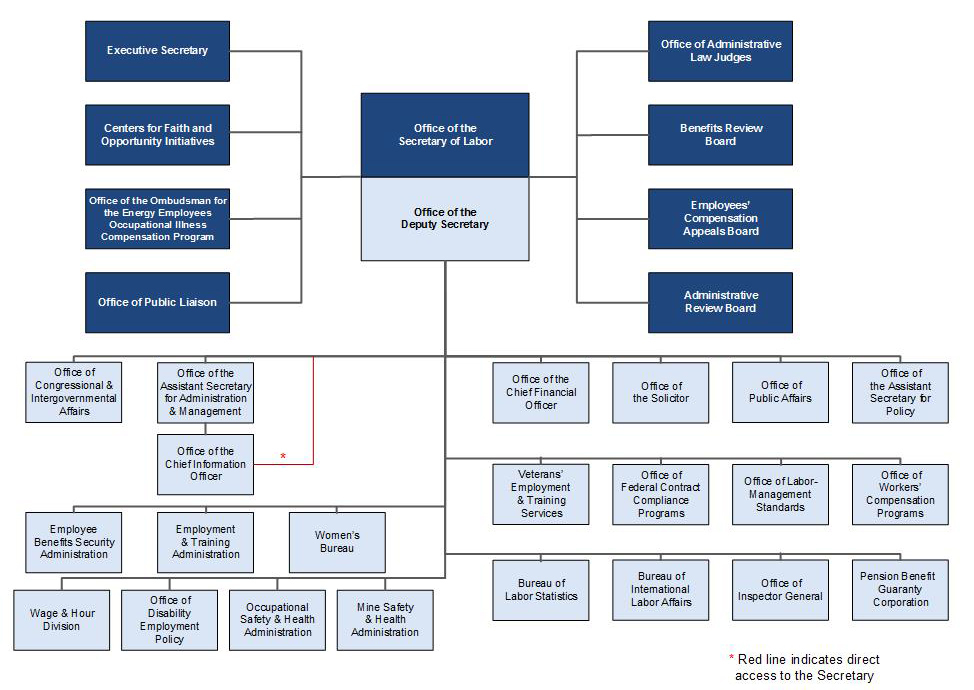
Information Security Organizational Chart Organizational Chart U S Department Of Labor.
Information Security Organizational ChartInformation Security Organizational Chart Gold, White, Black, Red, Blue, Beige, Grey, Price, Rose, Orange, Purple, Green, Yellow, Cyan, Bordeaux, pink, Indigo, Brown, Silver,Electronics, Video Games, Computers, Cell Phones, Toys, Games, Apparel, Accessories, Shoes, Jewelry, Watches, Office Products, Sports & Outdoors, Sporting Goods, Baby Products, Health, Personal Care, Beauty, Home, Garden, Bed & Bath, Furniture, Tools, Hardware, Vacuums, Outdoor Living, Automotive Parts, Pet Supplies, Broadband, DSL, Books, Book Store, Magazine, Subscription, Music, CDs, DVDs, Videos,Online Shopping