
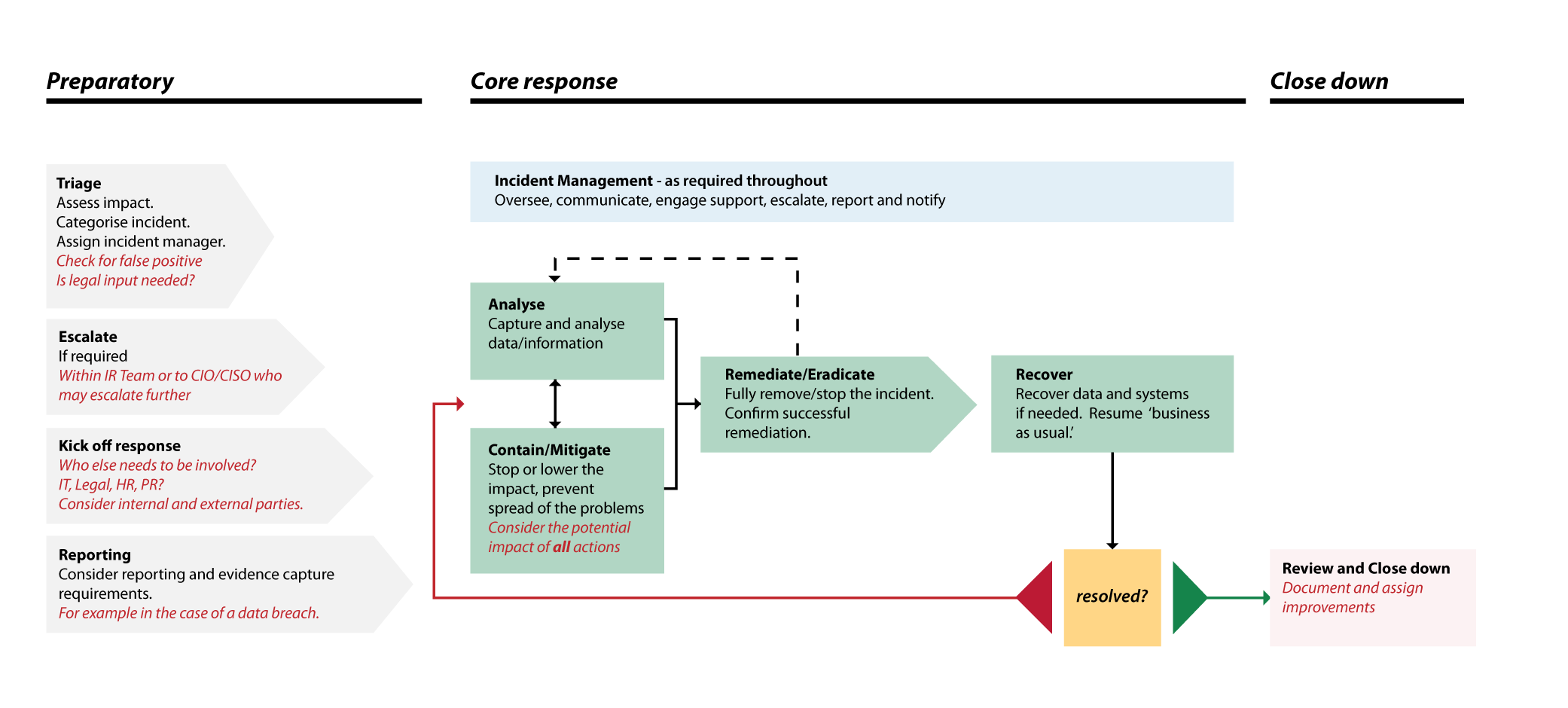
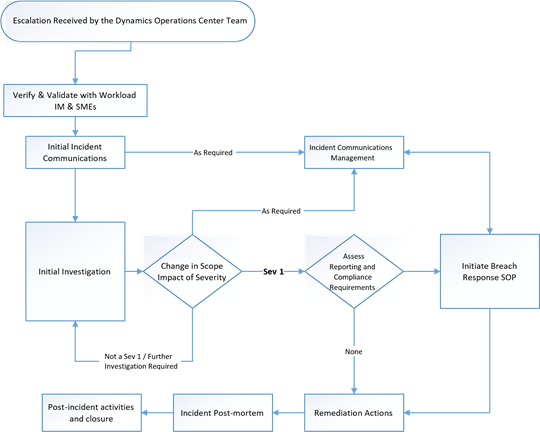
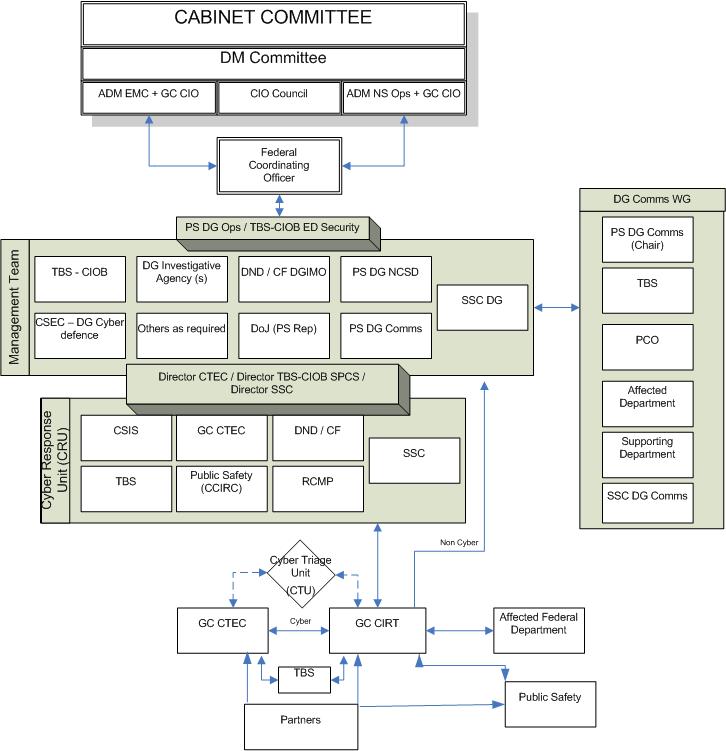
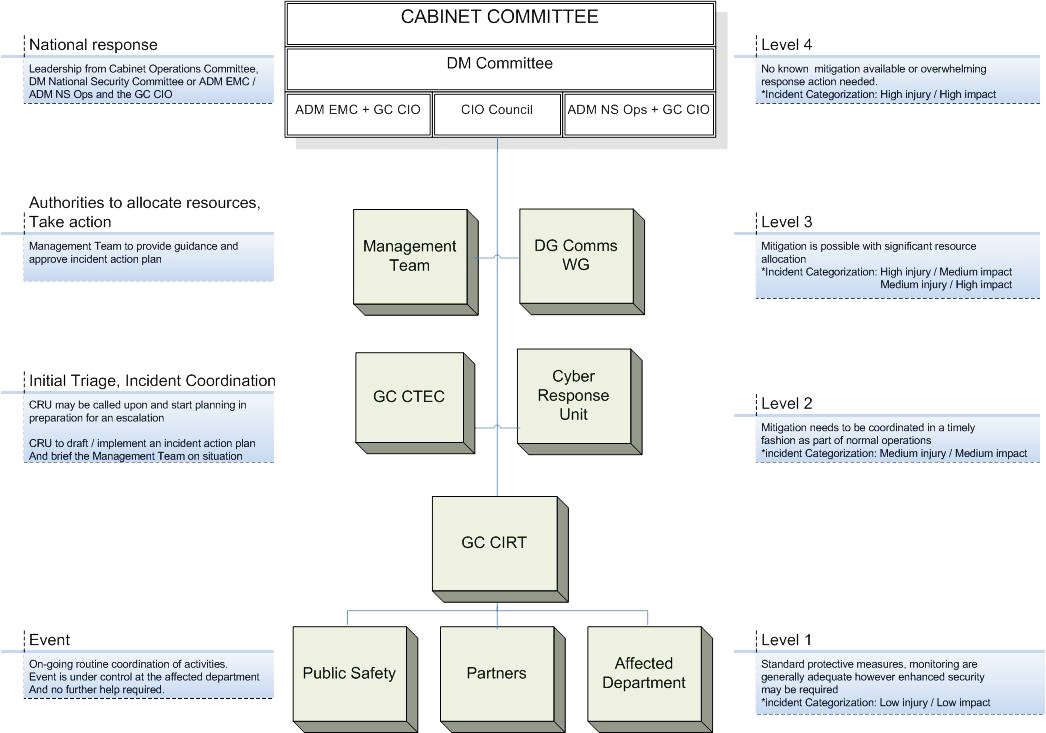
security incident reporting flow chart





































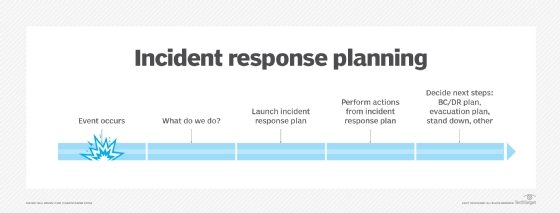


 How To Create A Cybersecurity Crisis Management Plan
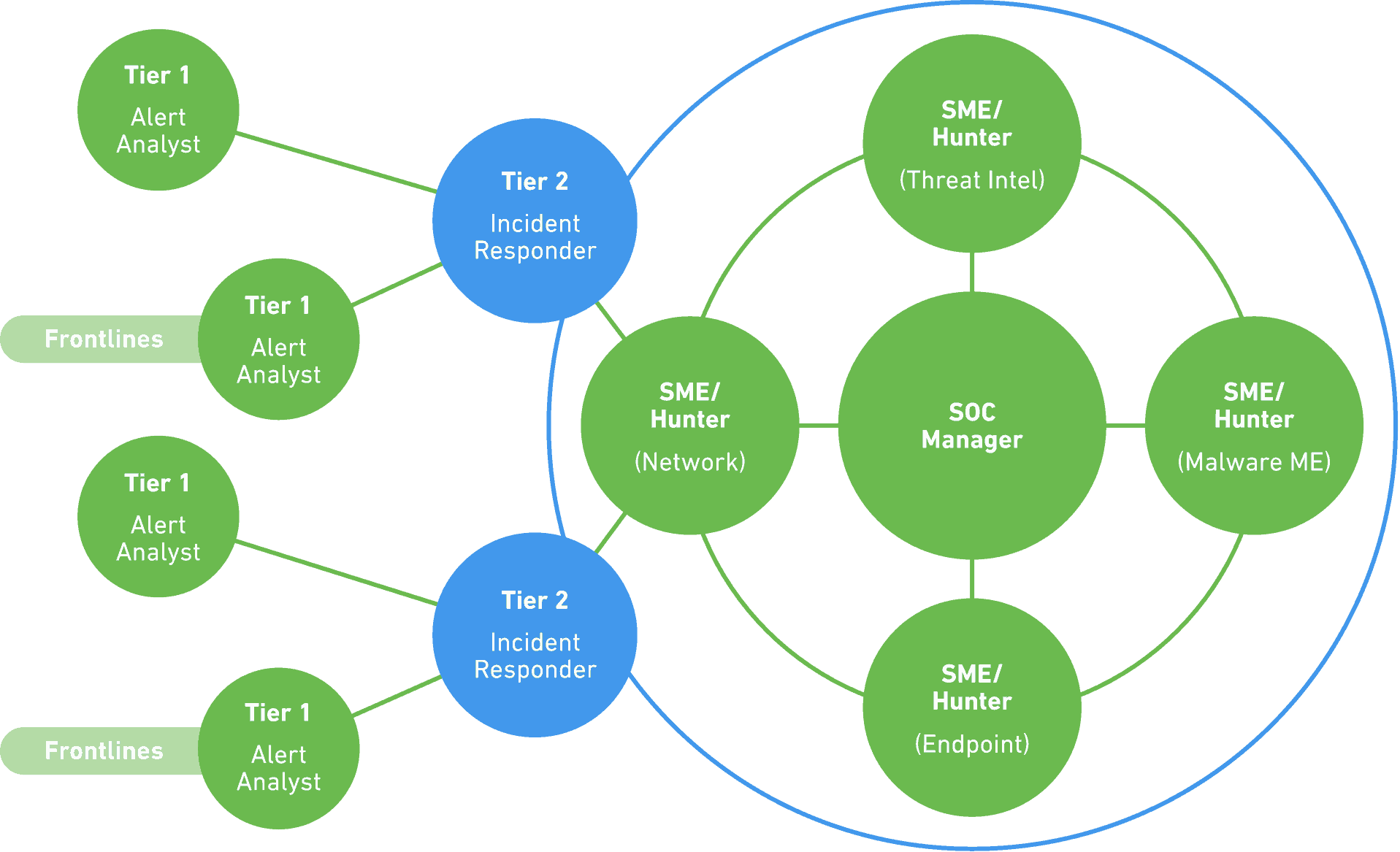
How To Create A Cybersecurity Crisis Management Plan Guidance For Setting Up A Cloud Security Operations Center.
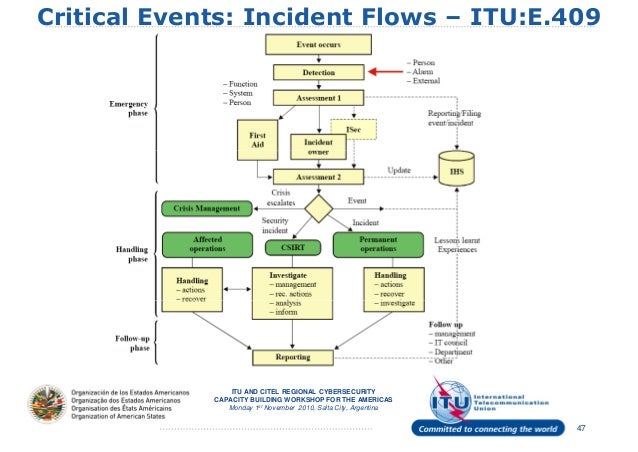
Cyber Incident Response Flow Chart Un Itu Organisational Structures And Incident Management.
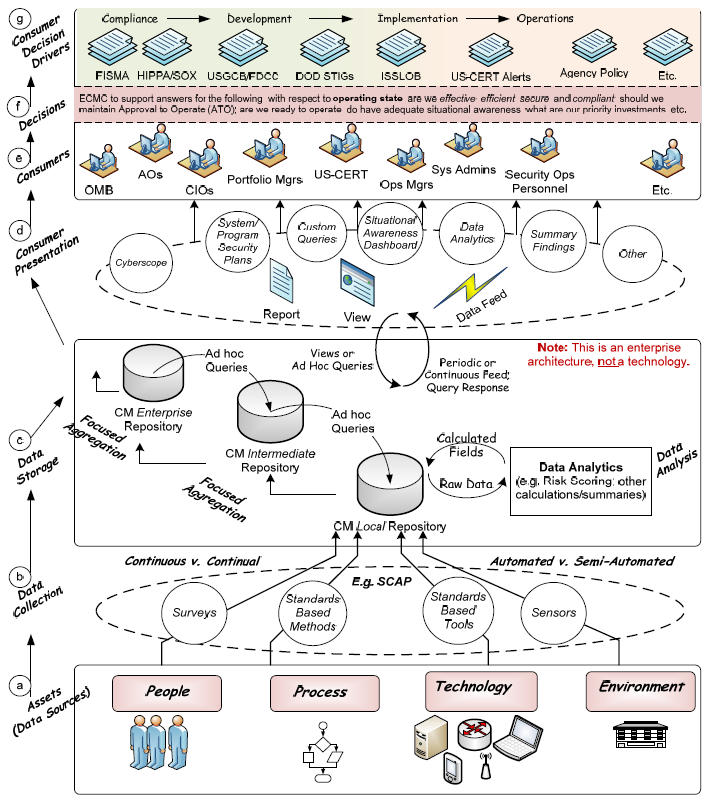
Cyber Incident Response Flow Chart Incident Management Guideline Queensland Government Chief.
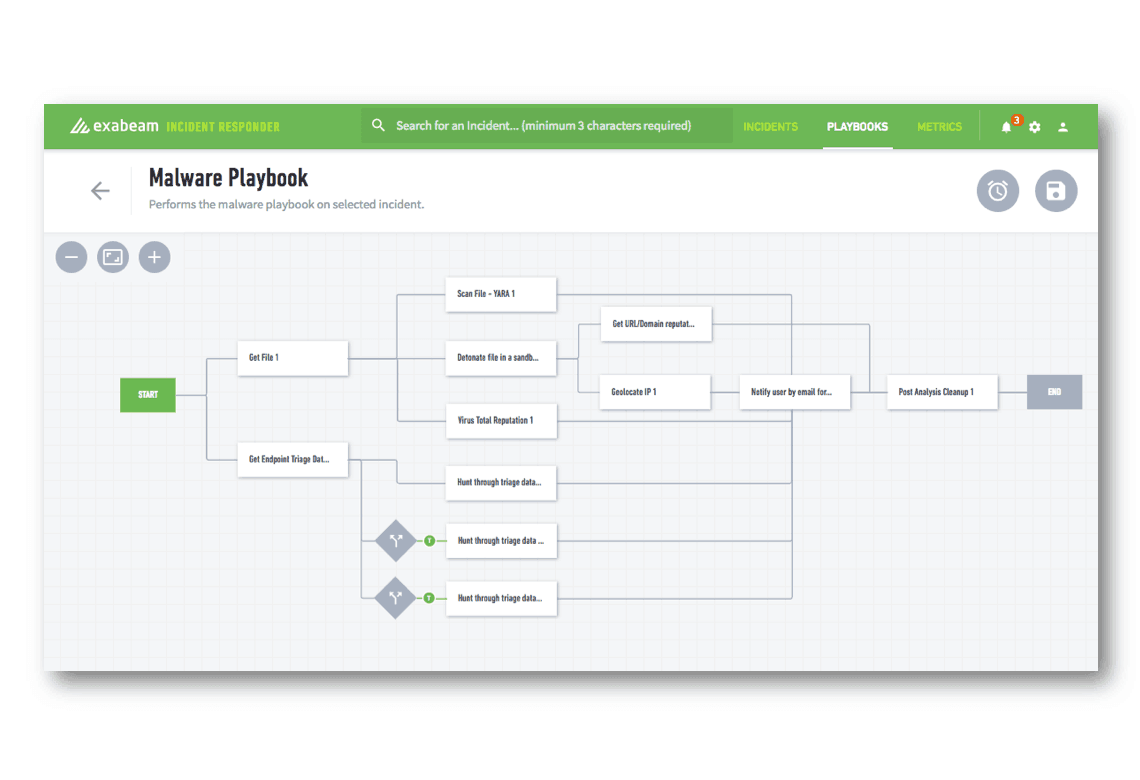
Cyber Incident Response Flow Chart Soc Secops And Siem How They Work Together.
Cyber Incident Response Flow ChartCyber Incident Response Flow Chart Gold, White, Black, Red, Blue, Beige, Grey, Price, Rose, Orange, Purple, Green, Yellow, Cyan, Bordeaux, pink, Indigo, Brown, Silver,Electronics, Video Games, Computers, Cell Phones, Toys, Games, Apparel, Accessories, Shoes, Jewelry, Watches, Office Products, Sports & Outdoors, Sporting Goods, Baby Products, Health, Personal Care, Beauty, Home, Garden, Bed & Bath, Furniture, Tools, Hardware, Vacuums, Outdoor Living, Automotive Parts, Pet Supplies, Broadband, DSL, Books, Book Store, Magazine, Subscription, Music, CDs, DVDs, Videos,Online Shopping