
september 2019 cyber attacks statistics hackmageddon














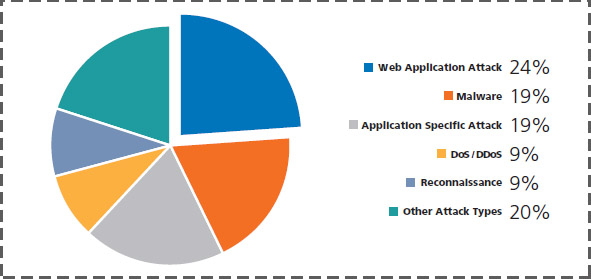
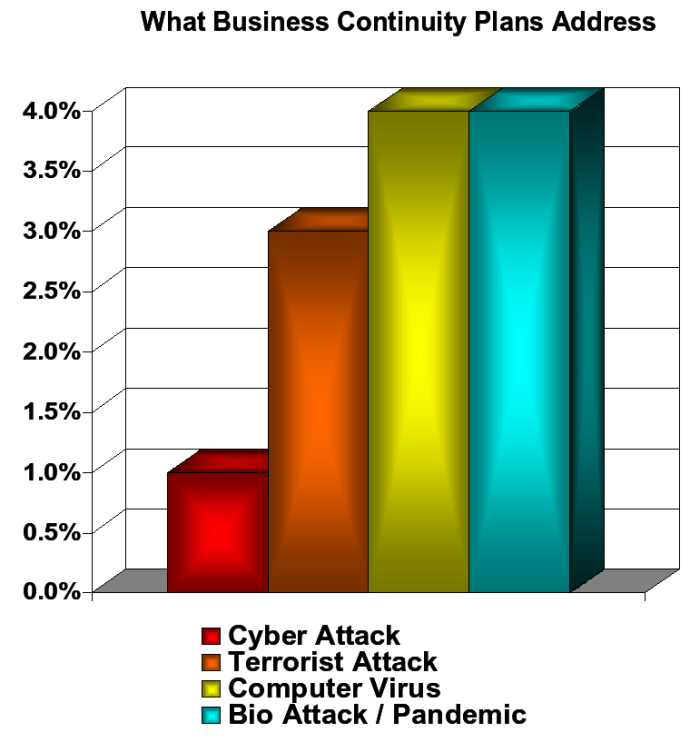




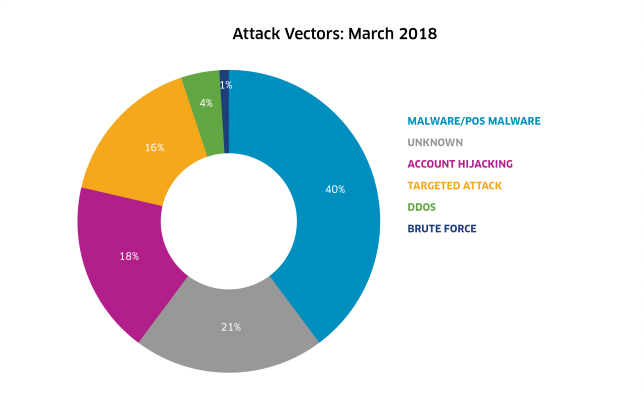


















 Cybersecurity Wbdg Whole Building Design Guide
Cybersecurity Wbdg Whole Building Design Guide June 2019 Cyber Attacks Statistics Hackmageddon.
Cyber Attack Chart Report K 12 Schools Experienced 122 Cyber Attacks In 2018.
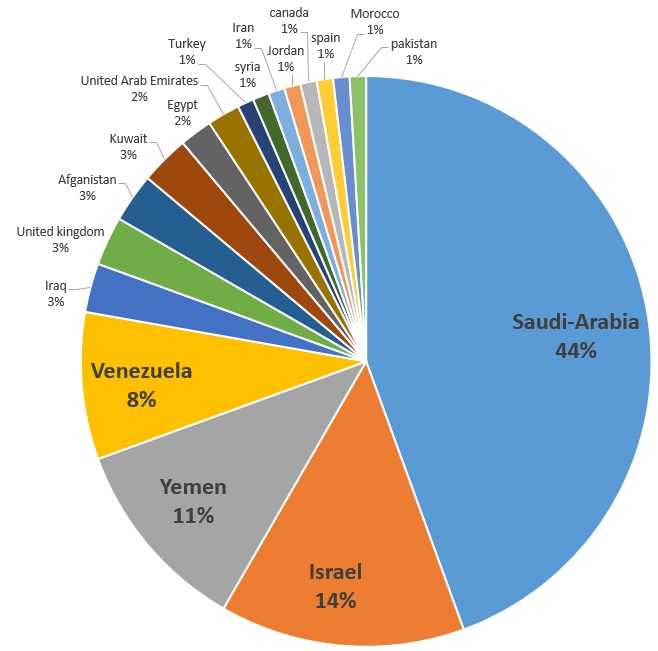
Cyber Attack Chart Iran Spying On Israel Saudi Arabia With Major Cyberattacks.
Cyber Attack Chart Insights Into The World Of Cyber Attacks By Scraping.
Cyber Attack ChartCyber Attack Chart Gold, White, Black, Red, Blue, Beige, Grey, Price, Rose, Orange, Purple, Green, Yellow, Cyan, Bordeaux, pink, Indigo, Brown, Silver,Electronics, Video Games, Computers, Cell Phones, Toys, Games, Apparel, Accessories, Shoes, Jewelry, Watches, Office Products, Sports & Outdoors, Sporting Goods, Baby Products, Health, Personal Care, Beauty, Home, Garden, Bed & Bath, Furniture, Tools, Hardware, Vacuums, Outdoor Living, Automotive Parts, Pet Supplies, Broadband, DSL, Books, Book Store, Magazine, Subscription, Music, CDs, DVDs, Videos,Online Shopping